by admin | Jan 18, 2025 | Hacking Tutorials
Introduction:Web applications are among the most common targets for cyberattacks. Ethical hackers must perform web application penetration testing to identify weaknesses before they can be exploited. This guide outlines a structured approach to conducting a web app...
by admin | Jan 18, 2025 | Hacking Tutorials
Introduction:Penetration testers rely on powerful tools to conduct thorough assessments of a network’s security. These tools help identify vulnerabilities and simulate real-world attacks. In this post, we’ll explore the five must-have tools for ethical hackers....
by admin | Jan 18, 2025 | Hacking Tutorials
Introduction:Ethical hacking is essential for securing systems against malicious attacks. As a beginner, it’s important to understand the core methods used by ethical hackers to identify and mitigate vulnerabilities. This post will cover the fundamental methods that...
by admin | Jan 18, 2025 | Hacking Tutorials
Overview: Introduce readers to ethical hacking, explaining its importance in securing systems and networks. Methods Covered: Reconnaissance (OSINT) Vulnerability scanning and assessment Password cracking and brute force testing Social engineering (with ethical...
by admin | Jan 12, 2025 | Hacking Tutorials
Chat NowEmail Us Share Full Spamming course, Have you ever wondered how people acquire access to bank logs and financial records, PayPal accounts, credit cards, email addresses, and other types of internet accounts? Here’s a quick guide to becoming a pro at spamming...
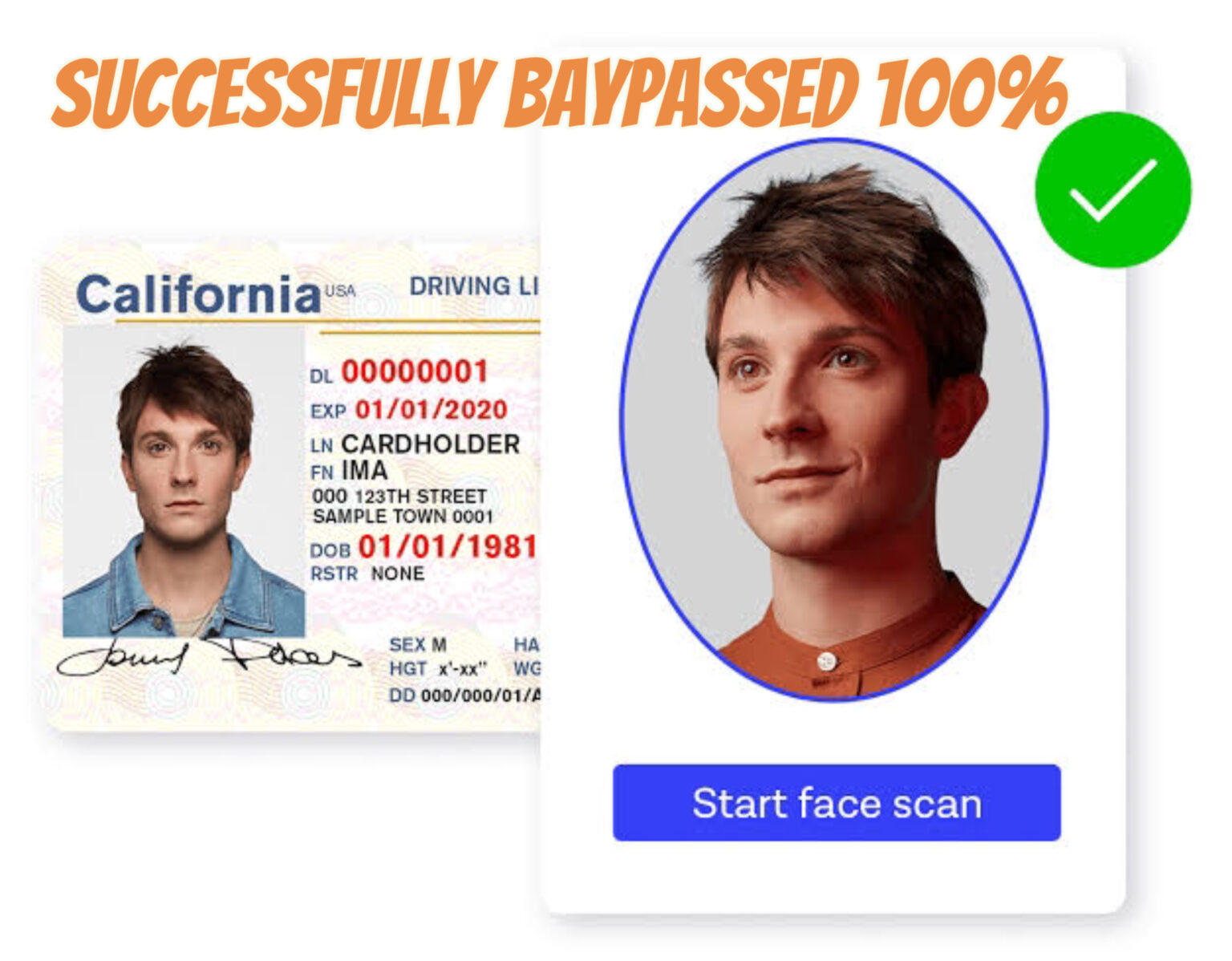
by admin | Jan 12, 2025 | Hacking Tutorials, Security
Chat NowEmail Us Share Hello there, Carders! In this article, I am aiming to share how to bypass KYC. I will go a head and show you how i succeeded in bypassing the KYC utilized by financial apps and small scale banks utilizing real-time deepfake and how these apps...



Recent Comments