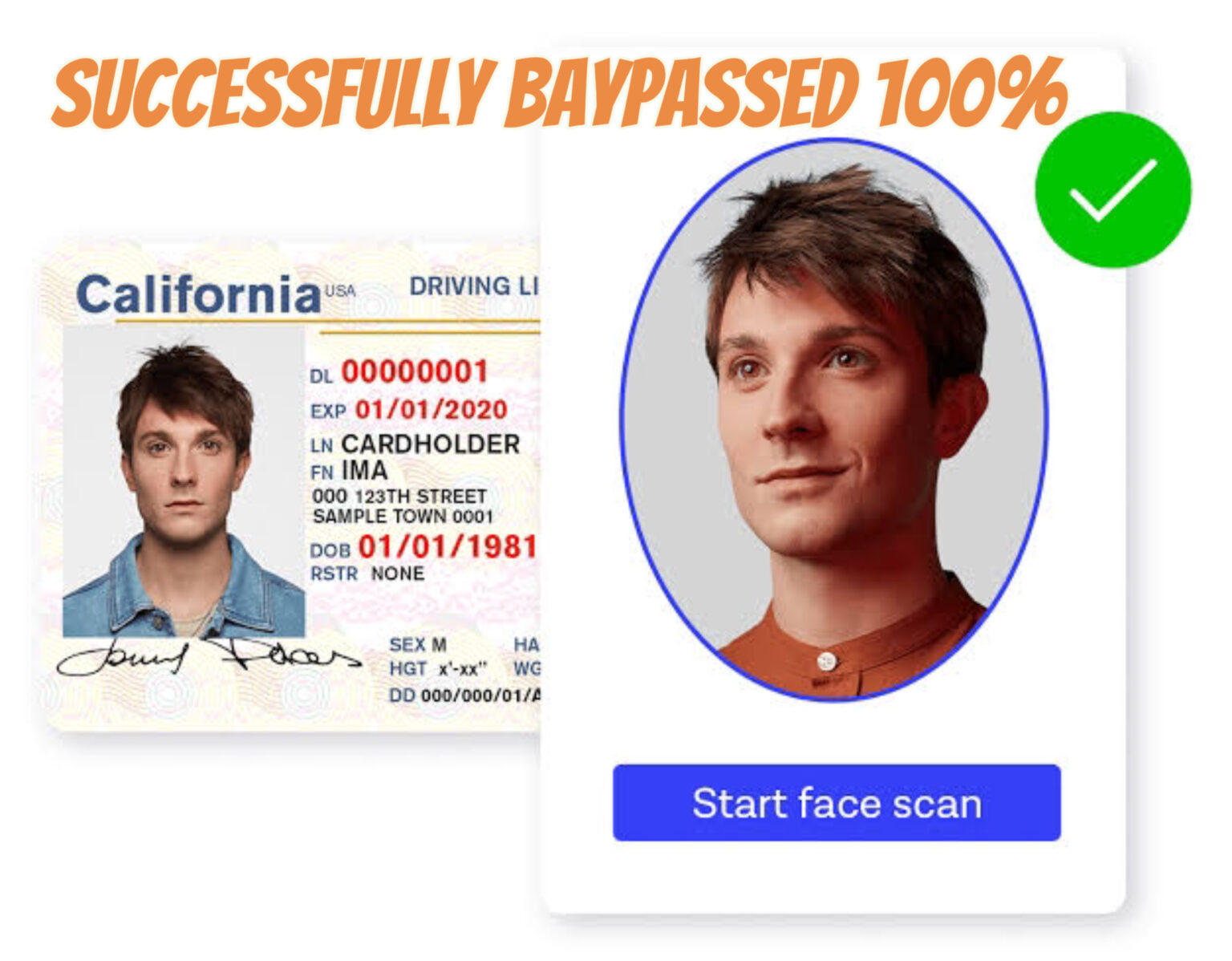
by admin | Jan 12, 2025 | Hacking Tutorials, Security
Chat NowEmail Us Share Hello there, Carders! In this article, I am aiming to share how to bypass KYC. I will go a head and show you how i succeeded in bypassing the KYC utilized by financial apps and small scale banks utilizing real-time deepfake and how these apps...

by admin | Jan 12, 2025 | Hacking Tutorials
Chat NowEmail Us Share As security technology and threat awareness among organizations improves so do the adversaries who are adopting and relying on new techniques to maximize speed and impact while evading detection. Join Private Telegram Channel Ransomware and...

by admin | Jan 12, 2025 | Hacking Tutorials
Chat NowEmail Us Share This is a 100% working tutorial of the Android hack where you can have the backdoor installed in any android device and have complete access to the device. I mean complete access, no kid! Join Private Telegram Channel This is not some Automated...
by admin | Jan 12, 2025 | Hacking Tutorials
Chat NowEmail Us Share The Tor network is an anonymous network that supports the existence of deep web and dark web websites. These websites can be surfed anonymously. This is only possible as the Tor network provides both security...

by admin | Jan 12, 2025 | Hacking Tutorials
In this article, we will delve into the methods used by hackers, also known as spammers, to acquire bank and credit card information. Please note that the information provided here is for educational purposes only and should not be used for illegal activities. Join...







Recent Comments